TrigID is the first and only Internet-based way to show that a real-world human is who they say they are. It enforces "one person, one identity" and you can verify that real-world identity with real-world identifiers like driver's license numbers, SSN's, addresses, phone numbers. All without giving anyone those identifiers. TrigID is a revolutionary, patent-pending "zero knowledge" validator of identity information inspired by geometric triangulation and its entire stucture is baked into public blockchain so it can't be hacked or faked.
TrigID is the number one and simplest Internet-primarily based absolutely totally way to show that a actual-global human is who they're announcing they will be. It enforces "one person, one identification" and you may affirm that actual-global identification with real-international identifiers like the use of pressure's license numbers, SSN's, addresses, cellphone numbers... All besides giving all and sundry those identifiers.
TrigID is a modern-day, patent-pending "zero facts" validator of identity information inspired with the beneficial useful useful resource of geometric triangulation and its whole stucture is baked into public blockchain so it cannot be hacked or faked.
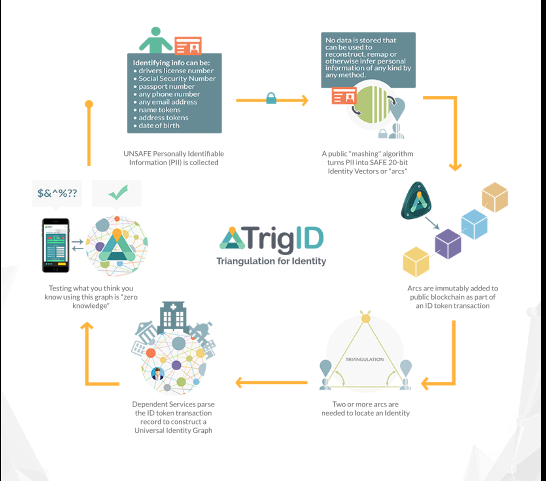
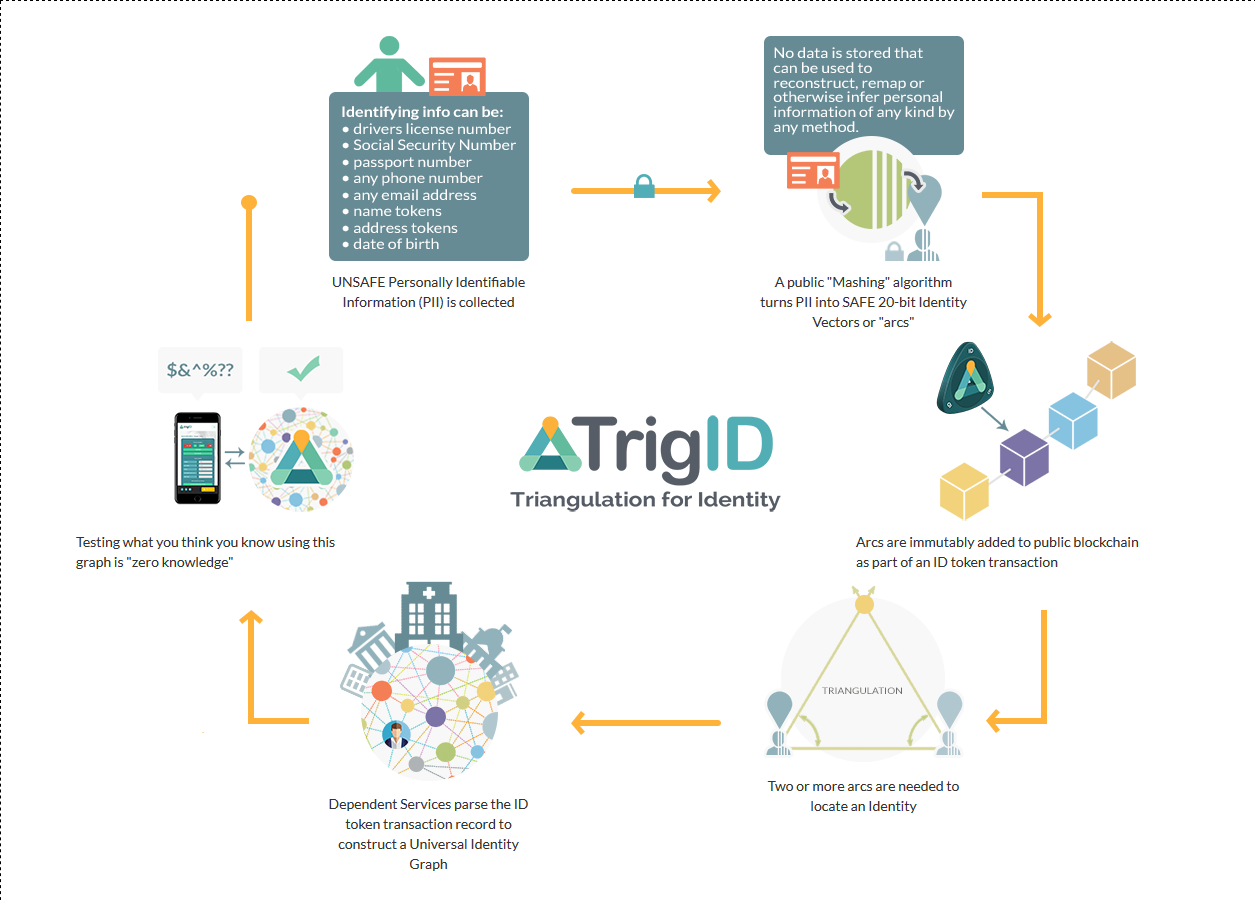
How It Works
TrigID uses a novel scheme, inspired by geometric triangulation. It takes common identifiers, encrypts them, then reduces their information content to 20 or fewer bits. This “mashing algorithm” makes what we call “Identity Vectors” that are really just arcs in a giant identity graph.
These arcs are no use by themselves. That’s why they can encoded into a public blockchain. One 20-bit Mash, for example, can represent more than 2000 possible tokens from identifiers of any type. That’s from the US alone, and it’s before third parties start adding things like medical record ID’s, tax file numbers…
These arcs are no use by themselves. That’s why they can encoded into a public blockchain. One 20-bit Mash, for example, can represent more than 2000 possible tokens from identifiers of any type. That’s from the US alone, and it’s before third parties start adding things like medical record ID’s, tax file numbers…
FEATURES OF THE PLATFORM
STRONG PROOF OF IDENTITY
Creating a few personal passphrases is a great way to allow a service locate you in their database, but it doesn't prevent people pretending to be you. A sophisticated bad actor can read the Mashes from blockchain and then give something that generates a collision. To prevent impersonation, you need to register a public key with the TrigID Identity Graph.
If a service wants to prove you're you, there are a few steps they need to take behind the scenes. They need to create a message, encrypt it with your public key, then get you to decrypt it with your passphrase (or private key).
If you don't trust the service with your phrase or private key even for the few milliseconds it takes to decrypt the message (and you shouldn't, unless it's an emergency) you can use a trusted key intermediary service or use an app that will decrypt the message and send it back to the service. The TrigID Personal app can do this for you.
ENSURING DATA INTEGRITY
The Curated ID Bounty Program provides a powerful incentive to load identities and their attributes. Those same bounties, however, are an incentive to load fake identities and attributes or attributes without sufficient notability.
This is one of the key reasons for giving an ID token a value and requiring that the ID be spent to deliver data. Most fraudulent submissions will be detectable using graph analysis techniques. Get caught and your bounties and your valuable submitted ID tokens will be forfeited.
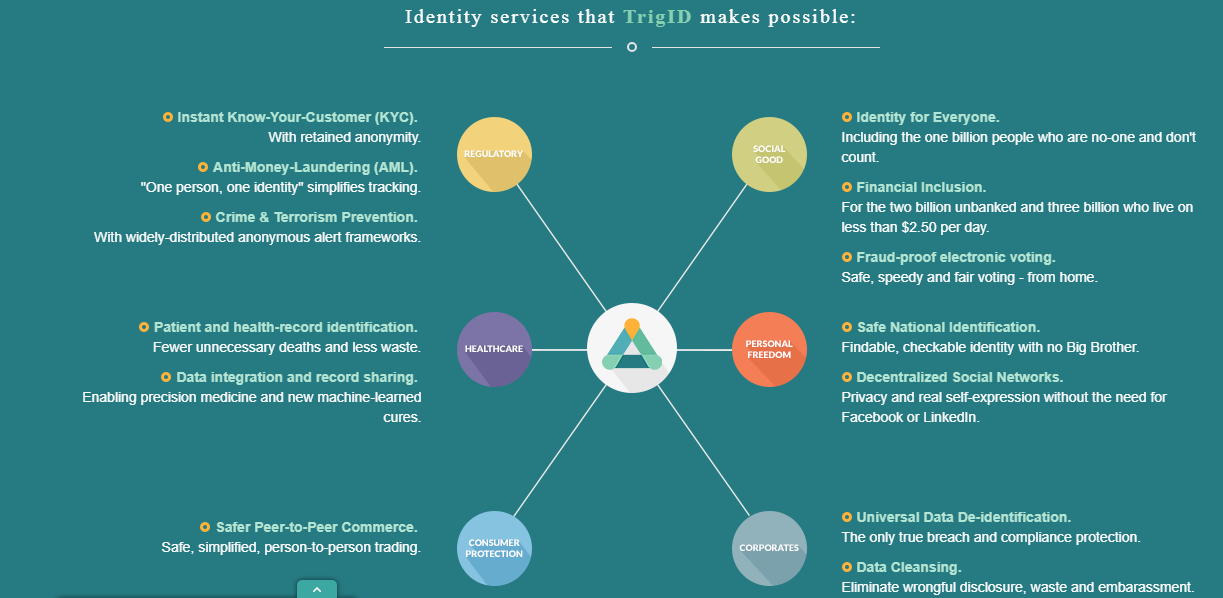
IDENTITY SERVICES INCLUDE
Automated Anonymous Know-Your-Customer (KYC)
Crime & Terrorism Prevention
Anti-Money-Laundering (AML)
Data integration and health record sharing
Patient and health-record identification
Safer Peer-to-Peer Commerce
Identity for Everyone
Financial Inclusion
Fraud-proof electronic voting
Safe National Identification
Decentralized Social Networks
Universal Data De-identification
Crime & Terrorism Prevention
Anti-Money-Laundering (AML)
Data integration and health record sharing
Patient and health-record identification
Safer Peer-to-Peer Commerce
Identity for Everyone
Financial Inclusion
Fraud-proof electronic voting
Safe National Identification
Decentralized Social Networks
Universal Data De-identification
Token Ecosystem
Any worthwhile identity service depends on the integrity of stored identity data. To keep this data up-to-date and maintain its integrity, each service needs to be able to add to, or change, the details of identities they service. To do that, they must pass their updates via a curation service. They need ID tokens.
To work with a TrigID curator, these identity services will need a reserve of tokens. Rather than repeatedly buying them on the open market, it makes sense that they should transact with tokens where possible. So they’ll encourage the people and organisations consuming those identity services to also transact using ID tokens.
This is a powerful and virtuous circle, and it’s the reason that we think that ID tokens can become “the” store of value for the online identity services economy.
Any foundation store of value needs stability — something that has been sorely-lacking in cryptocurrencies to date. To ensure this stability, the TrigID economy will run a Market Maker and use the Token Generation Event to provide it with a large pool of tokens to work with.
This Market Maker will also provide Token Venture Capital to selected identity service providers and Token Aid to identity-focused care organisations. Contact us if you’re a VC who’d like to help with this task.
TOKEN AND ICO DETAILS
ID tokens are a first-class TrigID crypto-infrastructure component. Each token can carry a set of "arcs" or "edges" – lines that connects facts in the Global TrigID blockchain database.
Think of these as the transactions in a database transaction log. When you transfer them, the ID transaction becomes part of the TrigID database. When someone wants to use the data, they parse the blockchain and assemble the TrigID graph the same way that a conventional database is assembled from a transaction log backup.
Sure, ID tokens carry value – but the value assigned to them provides economic incentive to build the global identity database. Holders who "spend" their tokens by putting arc data into them are rewarded with more ID tokens. This way the creation of the global identity graph can be crowdsourced.
You can get Whitelisted here: https://trigid.org/#
Discuss token valuation at https://forum.trigid.org/t/tokenomics
Discuss token valuation at https://forum.trigid.org/t/tokenomics
Token's initial value to be USD $1.00.
ROADMAP
TEAM


FOR MORE INFORMATION PLEASE VISIT THE LINKS I HAVE PROVIDED BELOW;
Website: https://trigid.org
Facebook: https://www.facebook.com/trigIDorg/
Twitter: https://twitter.com/TrigIDorg
Telegram: https://t.me/TrigID
LinkedIn: https://www.linkedin.com/company/trigid/
fa
Tidak ada komentar:
Posting Komentar